
Why Two Factor Authentication Is Important And What It Stops
Share
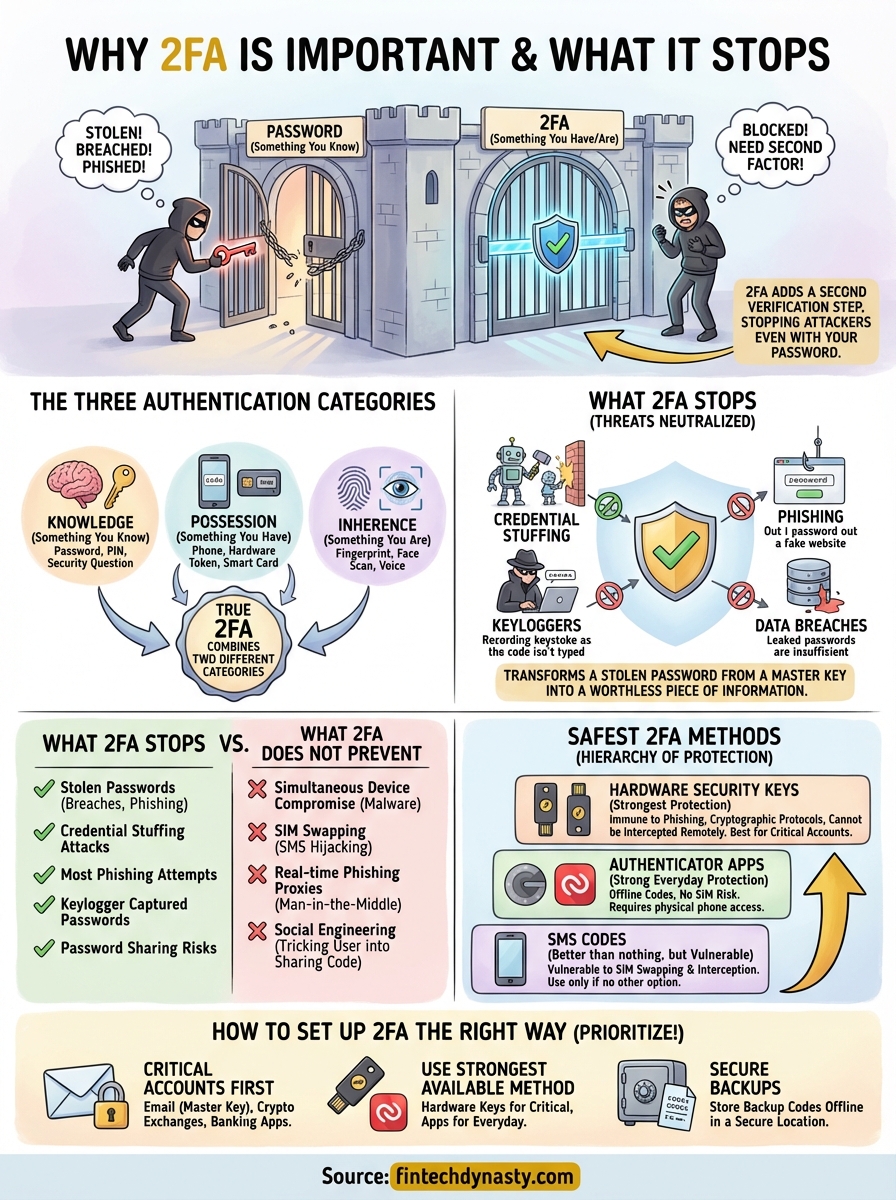
A password alone is no longer enough to protect your accounts. Hackers use credential stuffing, phishing, and data breaches to compromise millions of accounts every year, and once they have your password, they're in. This is exactly why two factor authentication is important: it adds a second verification step that stops attackers even when they've already stolen your login credentials.
Two factor authentication (2FA) requires you to prove your identity through something you know (your password) and something you have (like a phone or hardware device). This combination makes unauthorized access dramatically harder. For anyone holding cryptocurrency or managing financial accounts, 2FA isn't optional, it's a baseline security measure that stands between your assets and thieves.
At FinTech Dynasty, we focus on practical security education for crypto holders who want to protect their digital wealth without wading through hype or speculation. Understanding 2FA is a critical first step before moving into hardware wallets and self-custody solutions. This article breaks down how two factor authentication works, what threats it actually stops, and why it matters whether you're securing an exchange account or preparing to take full control of your private keys.
What two-factor authentication is
Two-factor authentication is a security process that requires you to verify your identity using two separate pieces of evidence before you can access an account or system. Instead of relying solely on a password (which can be stolen, guessed, or leaked in a data breach), 2FA adds a second checkpoint that attackers must overcome. This second factor typically comes from a different source than your password, making it exponentially harder for someone to break into your account even if they've compromised your credentials.
How the two factors work together
The first factor is almost always something you know, which is your password or PIN. The second factor is something you have or something you are. When you log in with your username and password, the system immediately prompts you for this second verification. You might receive a code via text message, approve a push notification on your phone, or insert a physical security key into your computer. The attacker would need to compromise both factors simultaneously to gain access, which is why two factor authentication is important for anyone serious about protecting their accounts.
Two-factor authentication turns your single point of failure into two independent barriers.
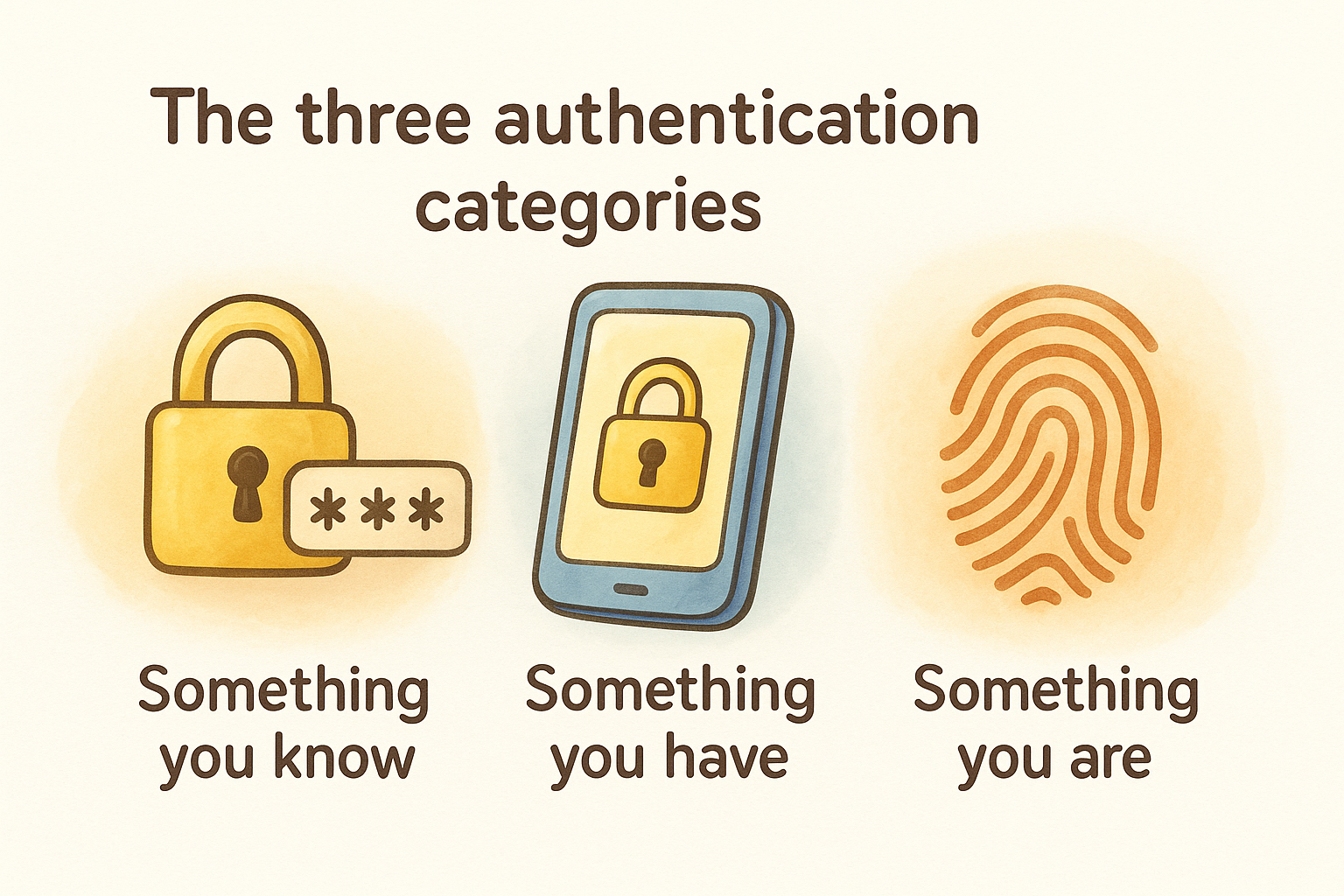
The three authentication categories
Security experts classify authentication factors into three distinct categories: knowledge (something you know, like a password), possession (something you have, like a phone or hardware token), and inherence (something you are, like a fingerprint or face scan). True 2FA combines two different categories to create layered protection. Your password and a security question don't count as 2FA because they're both knowledge factors. A password combined with a code from your phone does count because you're combining knowledge with possession. Understanding these categories helps you evaluate whether your accounts are truly protected or just using security theater.
Why two-factor authentication is important
Your accounts face constant threats that passwords alone cannot stop. Attackers have moved beyond simple guessing and now use automated tools that can test millions of stolen credentials per second against your accounts. Data breaches at major companies have exposed billions of username and password combinations, which criminals package into databases and sell on dark web marketplaces. When you understand that your password is likely already circulating in these databases, you begin to see why two factor authentication is important as a defense mechanism rather than a convenience feature.
Your password has already been compromised
You probably reuse passwords across multiple accounts or use variations that are easy to remember. Attackers know this. When a shopping site or forum gets breached and your credentials leak, criminals immediately test those same combinations on banking sites, crypto exchanges, and email providers. Even if you use unique passwords, phishing sites can capture them in real time. Two factor authentication protects you because stealing your password becomes insufficient for account access.
Your password stopped being a secret the moment any service you used got hacked.
Attack methods bypass passwords entirely
Keyloggers record every keystroke you make, capturing passwords as you type them. Session hijacking lets attackers steal active login sessions without ever needing your password. Credential stuffing tools automate login attempts using breached databases, and phishing campaigns trick you into entering credentials on fake login pages. Each of these methods treats your password as the only barrier to your accounts, which is exactly why 2FA transforms your security posture by requiring attackers to overcome a completely separate verification system.
What 2FA stops and what it does not
Two factor authentication creates a formidable barrier against the most common account takeover methods, but it's not bulletproof. Understanding exactly what threats 2FA neutralizes and where its protection ends helps you build a complete security strategy rather than treating it as a magic solution. This distinction becomes crucial when you're securing crypto accounts where a single mistake can mean permanent loss of funds.
Threats that 2FA blocks
2FA stops attackers who've obtained your password through data breaches, phishing sites, or keyloggers. When criminals test stolen credentials against your accounts, they hit a wall at the second authentication step. Credential stuffing attacks become useless because the automated bots can't generate or intercept your authentication codes. Password sharing risks drop significantly because anyone you've shared login details with still can't access your account without your phone or hardware key. This is exactly why two factor authentication is important for exchange accounts and email addresses tied to your crypto holdings.
2FA transforms your stolen password from a master key into a worthless piece of information.
What 2FA cannot prevent
Your 2FA protection fails when attackers compromise both factors simultaneously. If malware infects your phone and computer at the same time, criminals can steal passwords and intercept authentication codes in real time. SIM swapping attacks bypass SMS-based 2FA by convincing your carrier to transfer your number to a different device. Social engineering attacks that trick you into reading authentication codes to a fake support representative defeat the system entirely. Phishing sites sophisticated enough to proxy your login in real time can capture both your password and your 2FA code before you realize the site is fake.
Which 2FA methods are safest
Not all two factor authentication methods provide equal protection, and choosing the wrong type can leave you vulnerable to attacks that easily bypass weaker verification systems. The safest 2FA methods are resistant to phishing, cannot be intercepted remotely, and require physical possession of a device that attackers cannot duplicate from across the internet. Understanding this hierarchy becomes critical when you're protecting accounts that hold financial value or control access to your cryptocurrency holdings.
Hardware security keys offer the strongest protection
Physical security keys like YubiKey or Google Titan provide the highest level of 2FA security because they use cryptographic protocols that are immune to phishing attacks. When you insert the key into your computer or tap it against your phone, it generates a unique response that works only for the legitimate site you're trying to access. Fake login pages cannot trick these devices because the cryptographic handshake fails when the domain doesn't match. This protection explains exactly why two factor authentication is important for high-value accounts, and why hardware keys should be your first choice for exchange logins and email accounts tied to your crypto.

Hardware security keys cannot be fooled by even the most sophisticated phishing sites.
Authenticator apps provide strong everyday protection
Apps like Google Authenticator or Authy generate time-based codes on your phone that refresh every 30 seconds. These codes work offline and cannot be intercepted through SMS hijacking or SIM swapping attacks. Attackers would need physical access to your unlocked phone to steal codes, which makes authenticator apps significantly more secure than SMS while remaining convenient for daily use.
SMS codes are better than nothing
Text message verification stops basic attacks but remains vulnerable to SIM swapping and network interception. You should use SMS 2FA only when better options aren't available.
How to set up 2FA the right way
Implementing two factor authentication becomes effective only when you apply it strategically and configure it properly across your accounts. Many users enable 2FA on random services while leaving their most vulnerable accounts completely unprotected. Your approach should prioritize accounts based on their access to financial assets, their ability to reset passwords on other services, and the damage an attacker could cause if they gained control.
Start with your most critical accounts
Your email account controls password resets for every other service you use, making it the single most important account to protect with the strongest 2FA method available. Cryptocurrency exchanges, banking apps, and payment processors come next because they provide direct access to your funds. You should enable 2FA on these accounts before bothering with social media or shopping sites, regardless of how frequently you use them.
Your email account is the master key to everything else you own online.
Use the strongest method available
Choose hardware security keys for exchange accounts and email, authenticator apps for everyday services, and SMS only when no other option exists. You should configure backup authentication methods on critical accounts but store backup codes offline in a secure location rather than saving them digitally where malware could access them.
Keep your accounts protected
Two factor authentication transforms your security posture from vulnerable to defensible. You now understand why two factor authentication is important: it stops attackers even when they've stolen your password, blocks credential stuffing attacks, and neutralizes most phishing attempts. The implementation requires minimal effort but delivers maximum protection for your digital assets and financial accounts.
Your next step involves enabling 2FA on every account that holds value or controls access to other services. Start with your email account and cryptocurrency exchanges, then work through banking apps and payment processors. Choose hardware security keys for your most critical accounts, authenticator apps for everyday services, and avoid SMS codes whenever better options exist.
Building a complete security strategy requires more than 2FA alone. At FinTech Dynasty, we provide comprehensive guides on hardware wallet security, self-custody best practices, and the technical knowledge you need to protect your cryptocurrency holdings without relying on centralized platforms.
