
Two-Factor Authentication vs Multi-Factor Authentication
Share
Your cryptocurrency accounts are only as secure as the authentication protecting them. When comparing two-factor authentication vs multi-factor authentication, the distinction might seem like marketing jargon, but the technical differences matter more than most people realize. Understanding these security layers is essential for anyone serious about protecting digital assets.
Both 2FA and MFA add verification steps beyond a simple password, but they're not interchangeable terms. One is technically a subset of the other, and knowing which you're actually using can help you evaluate whether your current setup provides adequate protection. The right authentication method can mean the difference between a secure account and a compromised one.
This guide breaks down the core differences, explains when each applies, and helps you determine which authentication approach fits your security needs. At FinTech Dynasty, we focus on practical crypto security, and choosing the correct authentication method is foundational to protecting your self-custody setup.
Why authentication layers matter for crypto
Cryptocurrency accounts operate in a fundamentally different security environment than traditional banking. When someone gains access to your exchange account or self-custody wallet, they can move your funds instantly, and those transactions are irreversible by design. Banks can freeze accounts, reverse fraudulent transfers, and investigate suspicious activity. Your crypto assets don't have those safeguards. The authentication protecting your accounts is the only barrier between your holdings and an attacker.
Once your private keys or account credentials are compromised, there's no customer service number to call for a refund.
Authentication failures account for the majority of individual crypto losses outside of obvious scams. Hackers don't need to break sophisticated encryption when they can simply log in using stolen credentials. Your password alone provides minimal protection because data breaches expose billions of login combinations every year. Attackers test these credentials across cryptocurrency platforms systematically, knowing that successful access means immediate profit.
The irreversibility problem
Blockchain transactions finalize within minutes, and no central authority can reverse them once confirmed. This permanence is a core feature of cryptocurrency, but it creates severe consequences for compromised accounts. Traditional financial systems give you time to notice unauthorized activity and dispute charges. Crypto gives attackers a narrow window to drain accounts completely before you even realize something is wrong.
Your exchange account might hold thousands or millions of dollars in digital assets that can be converted to untraceable privacy coins and moved through mixing services within an hour. Self-custody wallets face similar risks if attackers gain access to your recovery phrases. Understanding two factor authentication vs multi factor authentication becomes critical because each additional authentication layer dramatically reduces the probability of successful unauthorized access.
Common attack vectors targeting credentials
Phishing attacks remain the most effective method for compromising crypto accounts. Attackers create fake login pages that look identical to legitimate exchanges, capturing your username and password when you enter them. They send urgent emails claiming your account faces suspension or offers limited-time rewards. Password-only security fails completely against these attacks because you're voluntarily providing your credentials to the attacker.

SIM swapping attacks target your phone number by convincing mobile carriers to transfer your number to a device the attacker controls. They can then receive SMS-based authentication codes and reset passwords on accounts tied to that phone number. Credential stuffing uses automated tools to test username and password combinations from previous breaches across multiple platforms. Layered authentication methods address these specific attack patterns by requiring proof that the person logging in actually controls multiple independent factors.
What authentication factors are
Authentication factors are distinct categories of evidence you provide to prove your identity when accessing an account. Security systems classify these factors into three separate types based on what they verify: something you know, something you have, or something you are. Each category operates independently, which means an attacker who compromises one factor still cannot access your account without the others.
The strength of any authentication system depends on using factors from different categories, not just adding more steps from the same category.
Understanding the difference between two factor authentication vs multi factor authentication requires recognizing how these categories work. Knowledge factors include passwords, PINs, or security questions that exist only in your memory. Possession factors require physical items you control, such as your smartphone, a hardware security key, or a smart card. Biometric factors verify unique physical characteristics like your fingerprint, facial structure, or iris pattern.
The three core authentication categories
Knowledge-based authentication is the weakest category because information can be stolen, guessed, or socially engineered. Passwords get compromised through data breaches, keyloggers, or phishing. Security questions often pull answers from publicly available information. Possession-based factors provide stronger security because attackers must physically obtain your device or security key. Your phone generates time-based codes through authenticator apps, or you might use a USB security key that creates cryptographic signatures. Biometric factors offer the highest resistance to remote attacks since they require your physical presence, though they can be spoofed with advanced techniques.
Why category diversity matters
Combining factors from different categories creates exponentially stronger protection than using multiple factors from the same category. Your password plus a security question both qualify as knowledge factors, so phishing attacks can capture both simultaneously. Adding an authenticator app code introduces a possession factor that requires accessing your physical device. This categorical separation forces attackers to use completely different attack methods for each factor.
Two-factor vs multi-factor vs two-step verification
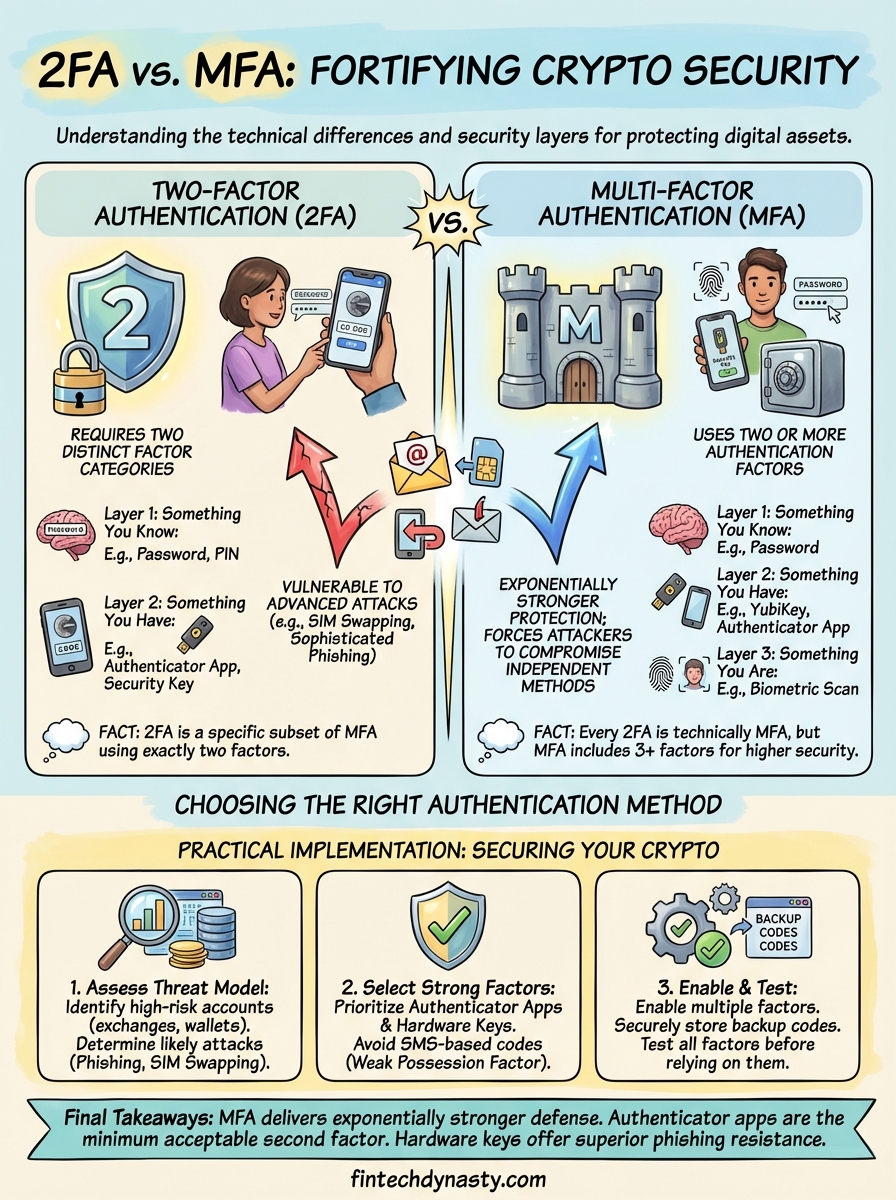
The terminology around authentication methods creates confusion that compromises security decisions. Two-factor authentication (2FA) specifically requires two distinct factors from different categories to verify your identity. Multi-factor authentication (MFA) is the broader umbrella term that includes any system using two or more authentication factors. Every 2FA implementation is technically MFA, but MFA can include three, four, or more factors depending on the security requirements.
Technical definition breakdown
Understanding two factor authentication vs multi factor authentication requires recognizing that 2FA is a specific subset of MFA using exactly two factors. When your exchange requires a password plus an authenticator app code, you're using 2FA. If that same platform adds biometric verification, you've moved into MFA territory with three factors. The distinction matters because security documentation often uses these terms interchangeably, leading you to believe you have stronger protection than actually exists.
Two-step verification gets confused with 2FA constantly, but they differ fundamentally. Two-step simply means your login process has two stages, which might use factors from the same category. An email verification code after your password qualifies as two-step verification, but both steps use knowledge factors. Real 2FA requires categorical diversity, pulling from separate authentication categories to prevent single-point compromise.
The number of steps in your login process doesn't automatically indicate stronger security unless those steps represent different factor categories.
Why the terminology confusion exists
Marketing teams blur these distinctions deliberately because "multi-factor authentication" sounds more sophisticated than admitting their platform offers basic two-factor protection. Service providers label two-step email verification as 2FA when it provides significantly weaker security than authenticator app codes. You need to examine what each authentication step actually verifies rather than trusting the label assigned to it.
Which option is safer in real attacks
Multi-factor authentication inherently provides stronger protection than two-factor implementations when facing real attack scenarios. The security advantage comes from forcing attackers to compromise additional independent factors, each requiring separate exploit techniques. When comparing two factor authentication vs multi factor authentication in actual breach attempts, systems using three or more factors demonstrate measurably lower compromise rates across documented security incidents.
Attack patterns that bypass weak authentication
Phishing attacks successfully capture both username and password combinations in single operations, defeating password-only security immediately. Adding SMS-based codes as your second factor still leaves you vulnerable because SIM swapping attacks can intercept those text messages through social engineering at mobile carriers. Attackers who control your phone number receive verification codes in real time, bypassing the second factor completely.
Authenticator app codes resist these attacks more effectively because they require physical device access rather than number control. Hardware security keys provide even stronger resistance since they use cryptographic signatures tied to specific websites, preventing phishing pages from capturing valid codes. Systems requiring three factors force attackers to compromise your password, gain physical access to your authenticator device, and potentially defeat biometric verification.
Adding a third authentication factor doesn't just make accounts slightly safer; it multiplies the attack complexity exponentially by requiring completely different compromise methods.
Credential stuffing and automated login attempts fail immediately against proper MFA because stolen passwords alone cannot bypass possession or biometric factors. The practical difference shows in platform breach reports where MFA-protected accounts face compromise rates below 0.1% compared to 15-30% for password-only or weak two-step verification systems.
How to choose and set up 2FA or MFA
Selecting authentication methods for your crypto accounts requires evaluating your specific threat model and understanding which factors provide protection against the attacks you're most likely to face. The debate around two factor authentication vs multi factor authentication becomes practical when you assess how attackers might target your holdings and which authentication combination blocks those specific techniques. Start by identifying your highest-risk accounts, typically exchanges holding significant balances or wallets containing recovery phrases.
Selecting the right authentication method
Authenticator apps (Google Authenticator, Authy) provide the minimum acceptable second factor for any cryptocurrency account because they resist SIM swapping and don't depend on carrier security. Hardware security keys like YubiKey offer superior phishing resistance through cryptographic verification that confirms you're on the legitimate website. You should avoid SMS-based codes entirely for crypto accounts since mobile carrier vulnerabilities make them the weakest possession factor available.
Prioritize authentication methods that require physical device access over those that rely on network-based delivery systems.
Implementation steps for crypto accounts
Enable your chosen authentication method through each platform's security settings, which typically appear under account security or privacy sections. Most exchanges support multiple simultaneous factors, letting you register both an authenticator app and hardware key for redundancy. Print and physically secure backup codes in a location separate from your device storage, treating them with the same protection level as recovery phrases. Test your authentication setup by logging out and verifying all factors work correctly before assuming your configuration is active.
Final takeaways
The choice between two factor authentication vs multi factor authentication determines your practical security level against real cryptocurrency threats. 2FA provides baseline protection through two distinct factor categories, while MFA adds exponential defense by requiring attackers to compromise three or more independent verification methods. You should implement authenticator apps as your minimum second factor and avoid SMS-based codes that remain vulnerable to SIM swapping attacks.
Your authentication configuration matters more than any other account security decision when protecting digital assets. Hardware security keys deliver the strongest protection available for high-value accounts, combining possession factors with cryptographic verification that blocks phishing attempts completely. Start by securing your most valuable exchange accounts with multiple factors, then apply the same approach to self-custody wallets and any platform controlling significant holdings. Learn more about comprehensive cryptocurrency security practices at FinTech Dynasty, where we focus on protecting your digital wealth through practical implementation rather than empty promises.
