
Private Key Encryption Explained: How Symmetric Keys Work
Share
Every time you send Bitcoin, sign a transaction, or access your hardware wallet, encryption is working behind the scenes to keep your assets safe. But the term gets thrown around loosely, and many crypto holders don't actually understand what's happening under the hood. Having private key encryption explained clearly matters, because your security decisions should be based on knowledge, not guesswork.
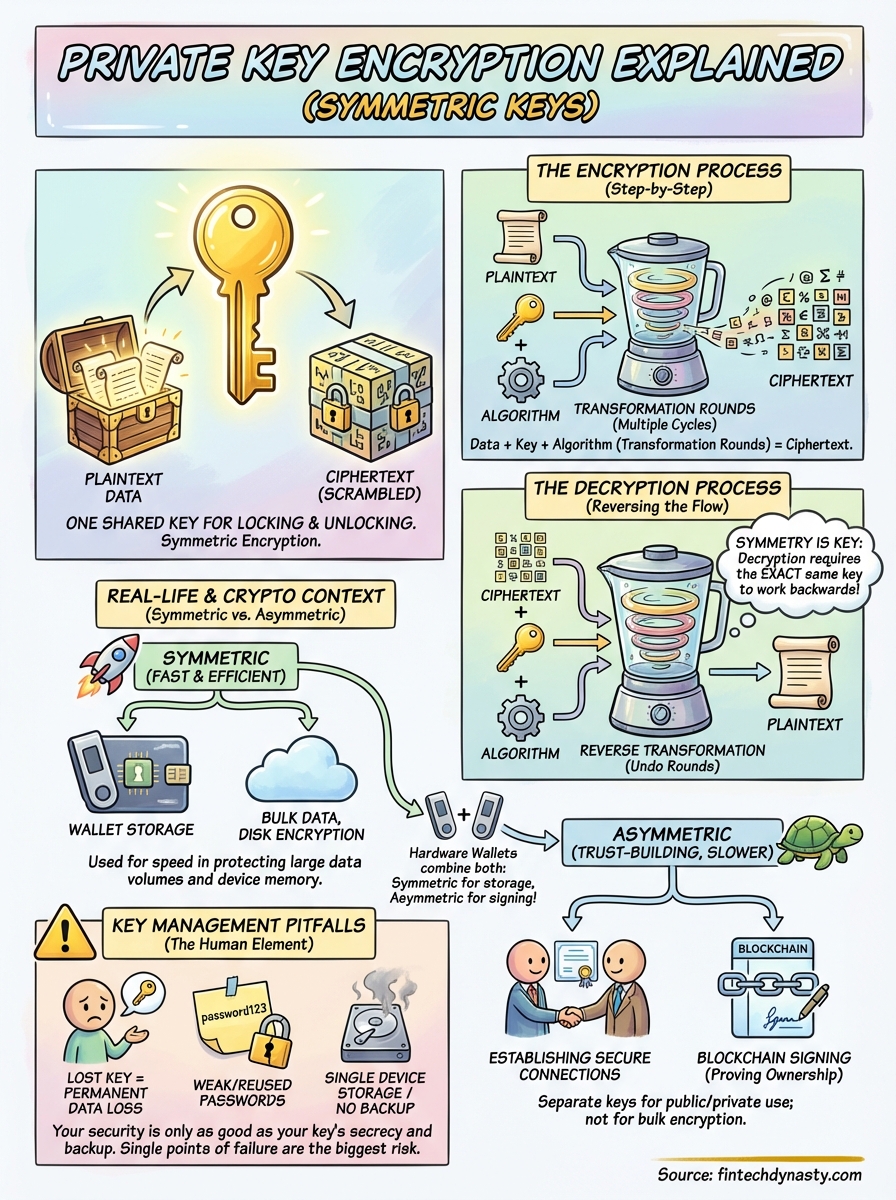
At its core, private key encryption (also called symmetric encryption) uses a single secret key to both lock and unlock data. This differs from the public-private key pairs you might associate with blockchain wallets. Understanding this distinction helps you grasp how your crypto is protected at multiple levels, from the firmware inside your hardware wallet to the encrypted backups storing your seed phrase.
This guide breaks down symmetric encryption in plain terms: how it works mechanically, where it fits into cryptocurrency security, and how it compares to asymmetric (public key) encryption. At FinTech Dynasty, we focus on giving you the technical foundation needed to make informed self-custody decisions. Whether you're evaluating cold storage devices or simply want to understand the technology protecting your holdings, you'll leave with practical knowledge you can actually use.
Why private key encryption matters
You rely on encryption every single day, even if you don't realize it. When you log into your bank account, send a private message, or store files in the cloud, symmetric encryption protects that data from unauthorized access. The same principle applies to cryptocurrency: your seed phrase recovery files, wallet backups, and communication with hardware devices all depend on private key encryption to stay secure. Without it, your digital assets would be exposed to anyone with network access or physical proximity to your storage device.
The foundation of digital security
Symmetric encryption forms the backbone of modern data protection because it's fast, efficient, and computationally simple compared to other methods. Banks use it to secure millions of transactions per second. Cloud storage providers use it to protect files at rest. Hardware wallets use it to encrypt your seed phrase before storing it in memory. The speed advantage matters when you're dealing with large amounts of data or need real-time processing, which is why symmetric algorithms like AES-256 remain the industry standard for bulk encryption.
Getting private key encryption explained properly helps you understand why certain security practices matter. For example, when a hardware wallet manufacturer claims "military-grade encryption," they're typically referring to symmetric algorithms that have been vetted and approved by organizations like the National Institute of Standards and Technology. These standards exist because weak or improperly implemented encryption has repeatedly led to catastrophic breaches.
The strength of your encryption is only as good as the secrecy of the key that controls it.
What breaks when encryption fails
History provides clear lessons about what happens when encryption implementations fail. The 2014 Heartbleed vulnerability exposed private keys across countless servers because of a flaw in the OpenSSL implementation. In 2017, the WannaCry ransomware attack exploited weak encryption practices to lock files on hundreds of thousands of machines. These weren't theoretical risks but real financial and data losses affecting individuals, hospitals, and corporations worldwide.
In the cryptocurrency context, poor key management has led to permanently lost funds more often than hacking attempts. When you encrypt a wallet backup with a weak password, or when you store an encrypted seed phrase without documenting the decryption method, you create single points of failure that no amount of blockchain security can fix. The encryption itself might be unbreakable, but if you lose the key or implement it incorrectly, your assets become inaccessible. Understanding these failure modes helps you avoid the mistakes that cost people their holdings.
How symmetric encryption works step by step
Symmetric encryption follows a straightforward process that uses one shared secret to both scramble and unscramble data. When you encrypt a file with a password, you're creating that single key which then gets mathematically combined with your original data through an encryption algorithm. The result is ciphertext: scrambled information that looks like random gibberish to anyone who doesn't possess the key. This method differs fundamentally from the asymmetric systems used for blockchain transactions, where separate keys handle encryption and decryption.
The encryption process
When you initiate encryption, the algorithm takes your plaintext data and your secret key as inputs. The algorithm then runs the data through multiple transformation rounds, substituting characters, shifting bits, and mixing information based on the key's unique values. Modern algorithms like AES perform these operations in 128, 192, or 256-bit blocks, repeating the process multiple times to ensure maximum security. Each round makes the output exponentially harder to reverse without the correct key.
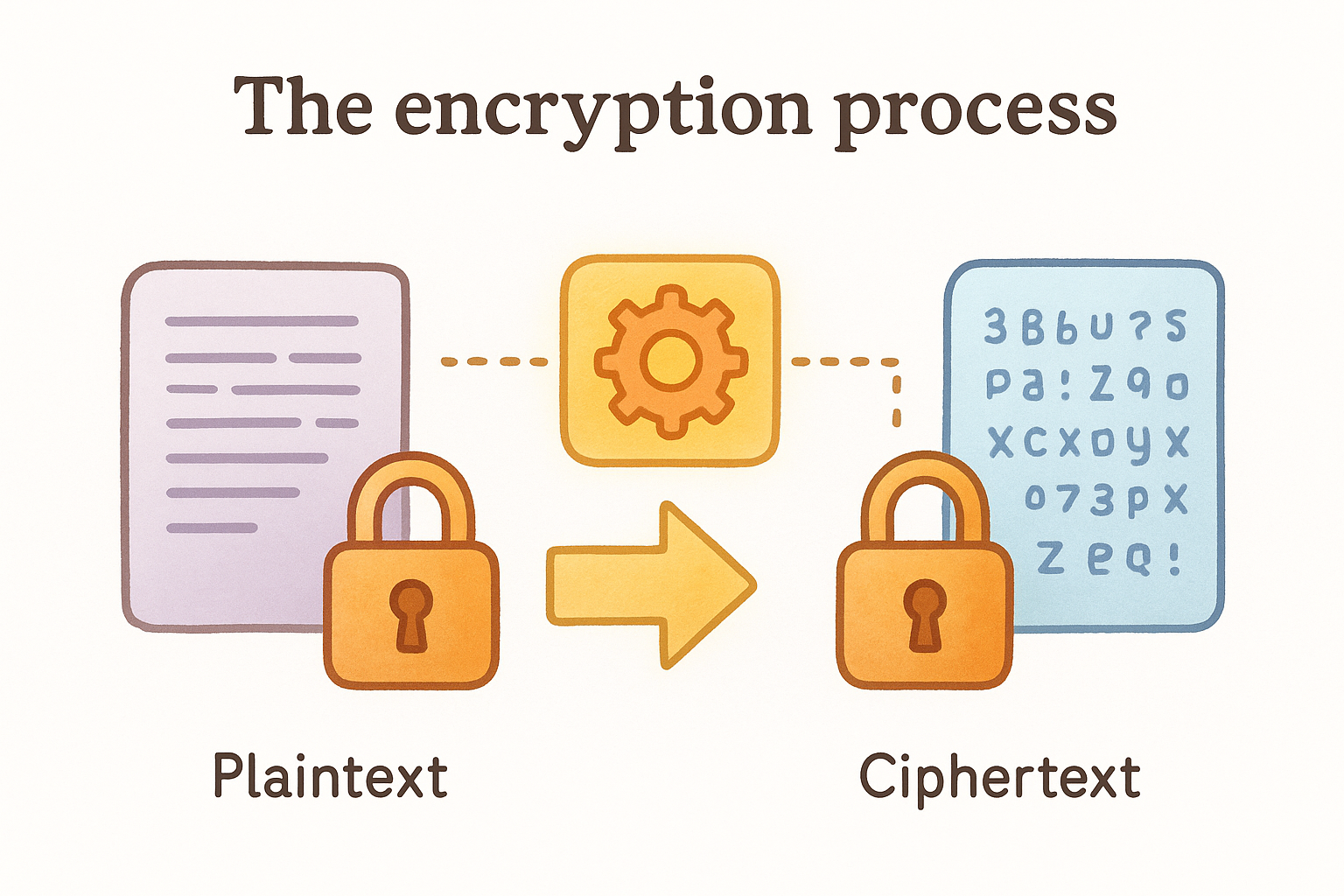
Your hardware wallet uses this same process when it encrypts your seed phrase before storing it in memory. The device generates or derives a key, applies the encryption algorithm, and produces ciphertext that remains secure even if someone physically accesses the chip.
Without the exact key used during encryption, reversing the process becomes computationally impossible within any reasonable timeframe.
The decryption process
Decryption reverses the encryption steps by applying the same secret key through the algorithm in reverse. The ciphertext gets fed into the algorithm alongside your key, and the system runs backward through the transformation rounds. Each step undoes the substitutions and shifts until the original plaintext emerges intact. This symmetry explains why the method gets called "symmetric" in the first place.
Getting private key encryption explained this way shows you why key storage matters so much. If you lose that single key, no amount of computational power will recover your encrypted data within a practical timeframe.
Symmetric vs asymmetric encryption in real life
Both encryption methods serve essential but different purposes in your daily digital life. Symmetric encryption handles the bulk of your data protection, from the files sitting on your hard drive to the video stream you're watching on Netflix. Asymmetric encryption steps in when you need to establish secure connections or verify identities without sharing secrets beforehand. Understanding when each method gets deployed helps you recognize why crypto wallets combine both approaches rather than relying on a single technique.
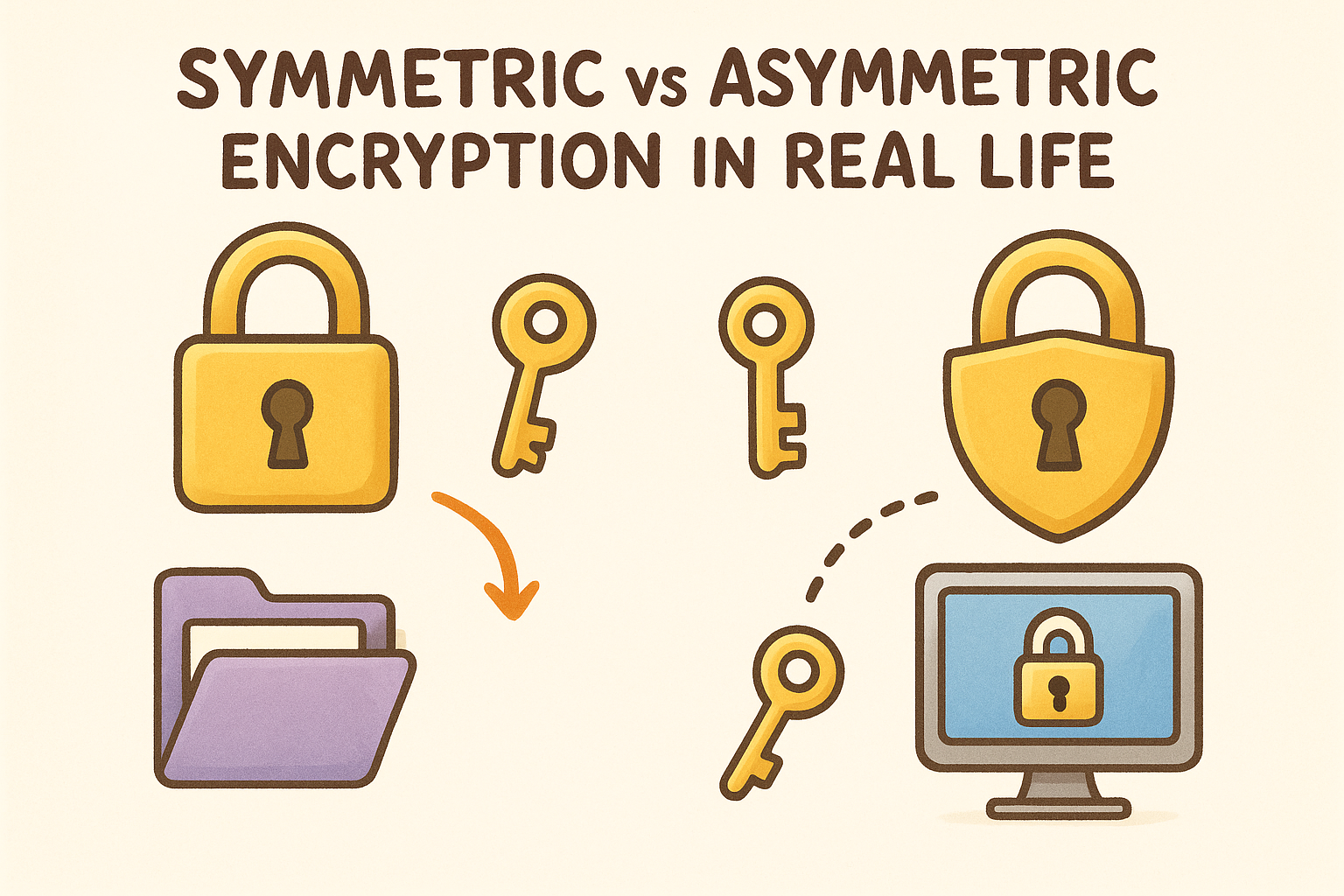
Where symmetric encryption dominates
Your operating system uses symmetric encryption to protect entire disk volumes because it needs speed above all else. When you encrypt a 500 GB drive, the system can't afford to run slow asymmetric operations on every single file read and write. AES-256 encryption can process gigabytes per second on modern hardware, making it the only practical choice for bulk data protection. Cloud storage providers follow the same logic: they encrypt your uploaded files using symmetric keys because asymmetric methods would create unacceptable performance bottlenecks.
Hardware wallets similarly rely on symmetric algorithms to encrypt seed phrases in memory. The device needs to decrypt that data quickly when you authorize a transaction, and symmetric operations deliver the necessary speed without compromising security.
When asymmetric encryption takes over
Asymmetric encryption solves the key distribution problem that symmetric methods can't handle alone. When you connect to your bank's website, your browser and the server use public key cryptography to establish a secure channel without ever sharing a secret key across the internet. Once that connection gets established, both sides typically switch to symmetric encryption for the actual data transfer because it's faster.
The best systems combine both methods: asymmetric encryption for establishing trust, symmetric encryption for protecting data at scale.
Getting private key encryption explained in this context shows you why blockchain transactions use asymmetric pairs: you need to prove ownership without revealing your secret, something symmetric encryption simply cannot accomplish.
Private keys in crypto: what they do and do not do
The term "private key" causes confusion because it means different things in different contexts. When you hear about private key encryption explained in a general computing sense, that refers to symmetric encryption where one secret unlocks data. But when crypto developers talk about private keys, they mean the asymmetric half of a keypair that authorizes blockchain transactions. These serve completely separate functions, and mixing them up leads to dangerous misunderstandings about how your wallet actually protects your assets.
What crypto private keys actually control
Your cryptocurrency private key functions as a mathematical signature generator, not an encryption tool in the traditional sense. When you initiate a Bitcoin transaction, your wallet uses the private key to create a unique digital signature that proves you authorized the transfer. This signature gets verified against your public key, which anyone can see on the blockchain. The private key never encrypts the transaction data itself because that information needs to remain publicly visible for network validation.
The private key in your crypto wallet proves ownership through mathematical proof, not by hiding information.
Your hardware wallet protects this asymmetric private key using symmetric encryption behind the scenes. The device encrypts the keypair data before storing it, which brings us full circle to the encryption methods discussed earlier.
What they don't encrypt or protect
Crypto private keys do not encrypt your transaction history, wallet balance, or blockchain activity. All of that information lives openly on the public ledger where anyone can view it by looking up your address. The private key only controls the ability to sign new transactions and move funds out of addresses associated with it. This distinction matters because beginners often assume that having a private key means their activity stays hidden, which fundamentally misrepresents how transparent blockchains operate.
Your seed phrase backup also doesn't get protected by the crypto private key itself. You need to apply separate encryption (typically symmetric) to secure that recovery information.
Key management basics and common failure modes
The security of your encrypted data depends entirely on how you protect the key itself. You can use unbreakable military-grade encryption, but if you lose the key or store it insecurely, the encryption becomes either worthless or a permanent barrier to your own data. This paradox explains why most encryption failures stem from human error rather than algorithmic weakness. Getting private key encryption explained means understanding both the technical protection and the practical vulnerability that key management introduces.
The single point of failure problem
Symmetric encryption creates an inherent risk because one key controls everything. When you encrypt your seed phrase backup with a password, that password becomes the single gateway to recovery. Store it in a text file on the same device and you defeat the entire security model. Write it on paper without documenting where it's stored and you risk permanent loss when memory fades or circumstances change. The same key that protects your data from attackers also blocks your own access if mishandled.
Your encrypted backup is only as recoverable as your key management system is reliable.
Common mistakes that cost people access
Password reuse ranks as the most frequent failure mode. When you protect your wallet backup with the same password you use for email, a breach at any service compromises all your encrypted data. Weak passwords that humans can remember also mean computers can crack them through brute force within reasonable timeframes. Conversely, generating truly random passwords without a documented recovery method leads to permanent lockouts when you forget or lose access to your password manager. Hardware failure represents another overlooked risk: storing your only key copy on a single device without backups means one drive failure erases access forever.
Key takeaways
Private key encryption explained comes down to understanding two fundamental concepts: symmetric encryption uses one shared secret to protect data at rest, while asymmetric keypairs in crypto prove ownership through mathematical signatures. Your hardware wallet combines both methods, using symmetric algorithms to encrypt your seed phrase in storage and asymmetric keys to authorize blockchain transactions. The strongest encryption becomes useless when you mismanage the keys themselves, which explains why proper key storage and documentation matter more than algorithm selection in most real-world scenarios.
Security knowledge beats assumptions every time. FinTech Dynasty provides detailed hardware wallet comparisons and practical guides that help you implement proper self-custody without the hype or speculation. Understanding how encryption actually protects your assets gives you the technical foundation needed to evaluate devices and make informed decisions about your holdings.
