
What Is Crypto Cold Storage? How It Works and Why It’s Safer
Share
When you buy cryptocurrency on an exchange, your assets sit on someone else's servers, exposed to hacks, platform failures, and policies you don't control. That's a problem if you're serious about protecting your holdings. Understanding what is crypto cold storage gives you a path to real ownership: keeping your private keys completely offline, away from internet-connected threats.
Cold storage is the foundation of self-custody. It's how long-term holders and security-focused investors keep their Bitcoin, Ethereum, and other digital assets safe from the vulnerabilities that plague online wallets and centralized platforms. At FinTech Dynasty, we focus on exactly this, helping you understand the technical side of securing your crypto without the noise of price speculation or trading hype.
This guide breaks down how cold storage works, why it offers stronger protection than hot wallets, and what options are available when you're ready to take control of your digital wealth.
Why crypto cold storage matters
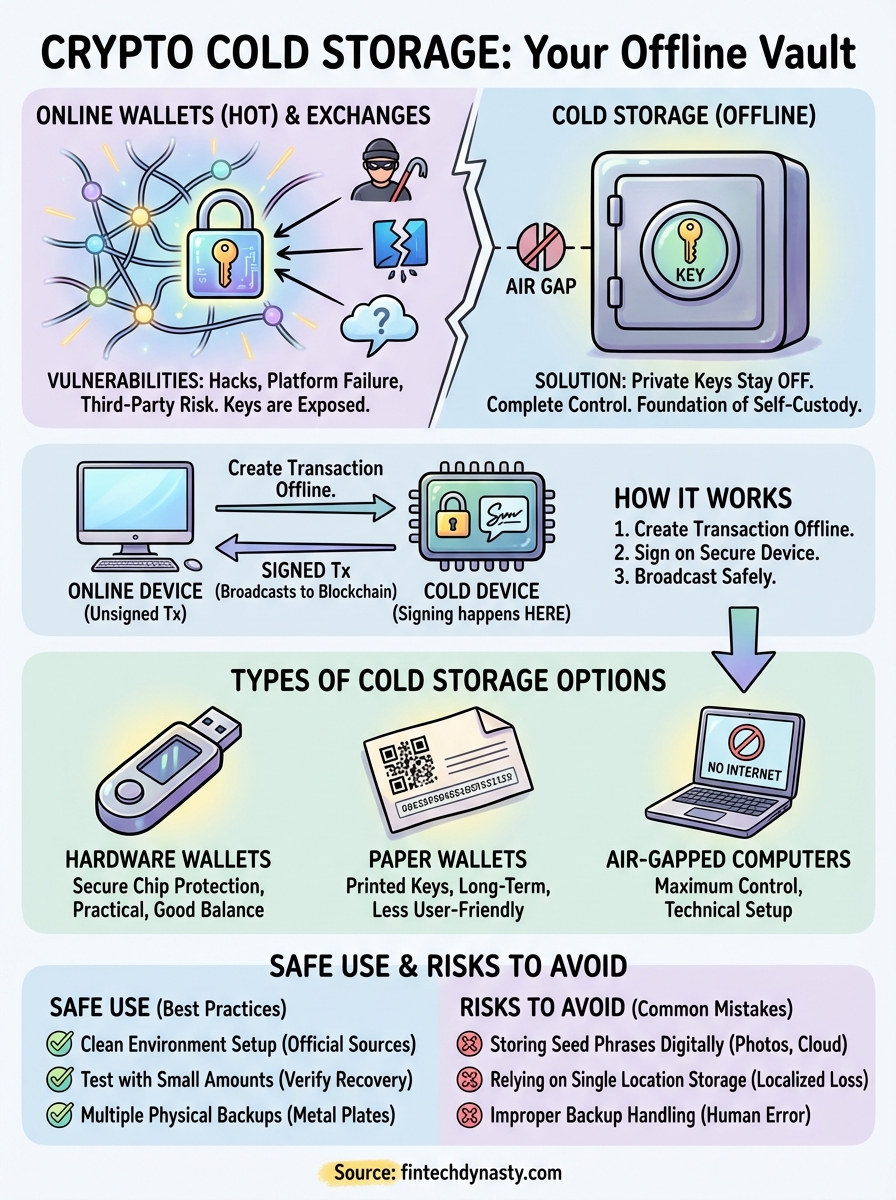
Your cryptocurrency is only as secure as the private keys controlling it. When you keep assets on an exchange or in a hot wallet, those keys sit on internet-connected servers where hackers, platform failures, and third-party policies can wipe out your holdings without warning. Cold storage removes that exposure entirely by keeping your private keys completely offline, disconnected from any network that could be compromised.
Exchange vulnerabilities expose your holdings
Exchanges handle billions in crypto daily, making them primary targets for sophisticated attacks. FTX collapsed in 2022, locking billions in customer funds. Mt. Gox lost 850,000 Bitcoin to theft. QuadrigaCX went down when its founder died with the only access to cold wallets. These aren't rare events, they're documented patterns showing that centralized platforms create single points of failure you can't control.
When you leave crypto on an exchange, you don't own the private keys. The platform does. That means your access depends on their security, their solvency, and their willingness to process your withdrawal when you need it most.
Hot wallets create permanent exposure
Hot wallets connect directly to the internet, which makes them convenient for frequent transactions but vulnerable to remote attacks. Malware can extract your seed phrase. Phishing sites can trick you into signing malicious transactions. Even legitimate software wallets face constant threats from zero-day exploits that haven't been patched yet.
Understanding what is crypto cold storage helps you see why offline protection eliminates these attack vectors entirely.
Cold storage gives you complete control
Cold storage transfers ownership from platforms and online services to you. Your private keys never touch an internet-connected device, so remote hackers have no digital pathway to your assets. You control when and how transactions happen. You choose your security model, whether that's a hardware wallet with secure chip protection or a paper wallet stored in a safe.
This matters most when you're holding crypto for the long term. If you're not actively trading, keeping keys online creates unnecessary risk. Cold storage lets you store with confidence, knowing that your assets remain protected even if exchanges fail, hot wallets get compromised, or new vulnerabilities emerge in connected systems.
How crypto cold storage works
Cold storage keeps your private keys physically separated from any internet-connected device. Your keys generate and remain on offline hardware or paper, never touching a computer that could transmit data to attackers. When you need to send crypto, you authorize transactions on the cold storage device itself, then transfer only the signed transaction to an online device for broadcasting to the blockchain.
Private keys stay permanently offline
The core principle is air gap security. Your cold storage device generates private keys in an isolated environment where no network connection exists. Those keys control your blockchain addresses, but they never leave the secure offline environment. Even when you check your balance, you're viewing public blockchain data, not exposing your private keys to connected systems.
Understanding what is crypto cold storage means recognizing that your keys never need internet access to maintain ownership of your assets.
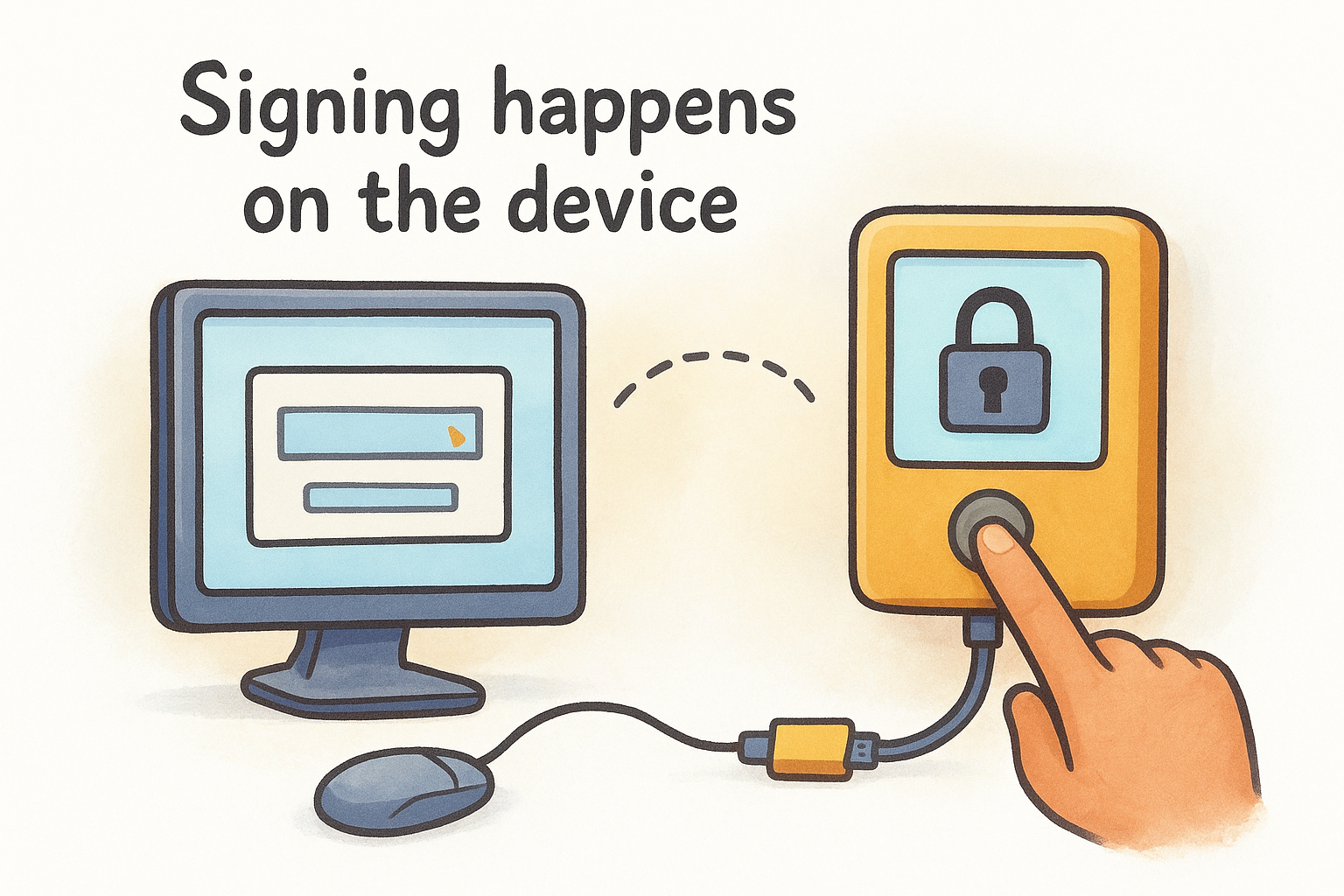
Signing happens on the device
When you want to send cryptocurrency, you create an unsigned transaction on your connected computer, specifying the recipient address and amount. You then transfer this unsigned transaction to your cold storage device (via USB, QR code, or SD card). The device uses your offline private keys to sign the transaction, proving you own the funds. Finally, you move the signed transaction back to your online computer, which broadcasts it to the network without ever exposing your keys.
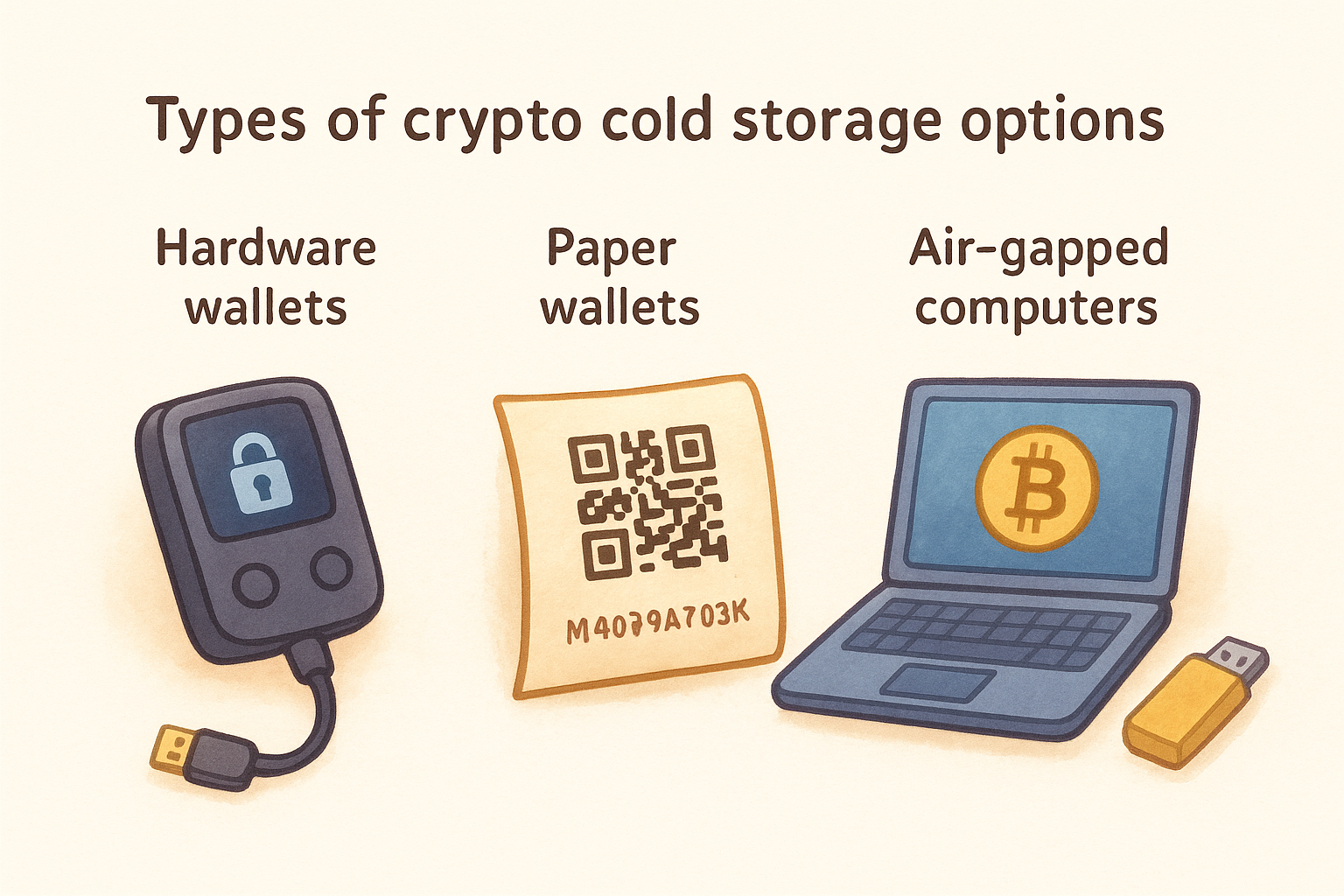
Types of crypto cold storage options
You have multiple cold storage methods to choose from, each with distinct security models and usability trade-offs. Hardware wallets dominate the market because they balance strong protection with practical access, but paper wallets and air-gapped computers offer alternatives depending on your technical comfort and storage timeline. The right choice depends on how often you need to transact and what level of physical security you can maintain.
Hardware wallets
Hardware wallets store your private keys on dedicated secure chips that never expose keys to connected devices. Ledger and Trezor use certified security elements that protect against physical tampering and firmware attacks. You plug the device into your computer via USB, authorize transactions on the device screen itself, and unplug it when finished. These devices support hundreds of cryptocurrencies and integrate with standard wallet interfaces, making them the most practical option for users who need regular access without compromising security.
Hardware wallets give you the strongest balance between security and convenience when managing multiple assets.
Paper wallets
Paper wallets are printed private keys that you generate offline and store physically. You create them using software on an air-gapped computer, print the QR codes and alphanumeric keys, then destroy all digital traces. Paper wallets work best for long-term storage where you don't need frequent access. The risk comes from physical damage, loss, and the complexity of securely generating keys without exposure to compromised printers or generation software.
Air-gapped computers
Air-gapped computers are dedicated devices that never connect to any network. You install wallet software, generate keys offline, and transfer signed transactions using USB drives or QR codes. This method offers maximum control but requires technical knowledge to maintain true isolation and avoid cross-contamination from infected media.
How to use crypto cold storage safely
Using cold storage correctly requires following specific setup and maintenance practices that prevent key exposure during initial configuration and future transactions. You need to establish security from the first moment you generate keys, verify everything works before committing large amounts, and maintain clear recovery documentation that doesn't compromise your private information.
Set up in a clean environment
Your cold storage setup happens on devices that could already be compromised. Download wallet software or firmware updates only from official sources, verify cryptographic signatures when available, and use a dedicated computer that hasn't been exposed to suspicious downloads or websites. For hardware wallets, check for physical tampering indicators on packaging and devices. Avoid public WiFi during setup, and disconnect from the internet when generating seed phrases on any device that isn't designed to stay permanently offline.
Test with small amounts first
Before moving significant holdings, send a small test transaction to verify you can access the funds. Write down your seed phrase, initialize the device, then perform a full recovery to confirm your backup works correctly. This step catches errors in how you recorded your recovery information before your entire portfolio depends on it. Understanding what is crypto cold storage means recognizing that proper testing prevents catastrophic loss from backup mistakes.
Testing recovery procedures with minimal funds protects you from discovering backup failures after it's too late.
Document your recovery plan
Store your seed phrase in multiple physical locations using methods that protect against fire, water, and theft. Metal backup plates resist environmental damage better than paper. Never photograph your seed phrase or store it digitally. Create clear instructions for trusted individuals who might need to recover your assets if something happens to you, without revealing the actual keys in those instructions.
Risks and common mistakes to avoid
Cold storage eliminates online threats, but it creates new vulnerabilities you need to manage directly. Physical loss, human error, and improper backup handling can lock you out of your funds permanently. You control the security, which means you're responsible for mistakes that no customer service team can reverse. These risks aren't theoretical, they represent the most common ways people lose access to cold-stored cryptocurrency.
Storing seed phrases digitally
Taking photos of your seed phrase, saving it in cloud storage, or typing it into password managers defeats the entire purpose of cold storage. Any digital copy creates an attack surface where malware, data breaches, or unauthorized access can compromise your keys. Email, messaging apps, and note-taking software all sync across devices and servers you don't control, exposing your recovery information to the same threats you're trying to avoid.
Digital copies of your seed phrase turn cold storage into hot storage with extra steps.
Store your recovery information on physical media only, using metal plates for durability or paper kept in fireproof containers. Never photograph backup materials, even temporarily.
Relying on single location storage
Keeping your only seed phrase backup in one location creates a single point of failure. House fires, floods, theft, and simple misplacement can eliminate your only path to recovery. You need multiple physical copies stored in separate geographic locations, protected against both environmental damage and unauthorized access. Understanding what is crypto cold storage includes recognizing that proper redundancy prevents total loss from localized disasters.
Where to go from here
You now understand what is crypto cold storage means in practice: offline private key management that eliminates the attack vectors plaguing exchanges and hot wallets. The next step is choosing your specific cold storage method, whether that's a hardware wallet with secure chip protection, a paper wallet for long-term holding, or an air-gapped computer for maximum control. Each option requires careful setup, proper backup procedures, and ongoing physical security maintenance.
FinTech Dynasty provides detailed hardware wallet comparisons and security tutorials to help you implement cold storage correctly. You'll find side-by-side evaluations of major devices, step-by-step setup guides, and practical checklists for avoiding common mistakes that lock people out of their funds. Start with small amounts, verify your recovery process works, then scale up as your confidence grows. Taking control of your private keys means accepting full responsibility for security, but it's the only path to true ownership of your digital assets.
