
Hot Wallet Vs Cold Wallet: Security Tradeoffs Explained Fast
Share
Your crypto sits somewhere right now, either connected to the internet or completely offline. That single distinction defines the hot wallet vs cold wallet debate, and it carries real consequences for your security.
Hot wallets offer speed and convenience. Cold wallets prioritize protection above all else. Neither option is universally "better", the right choice depends on how you use your crypto, how much you hold, and what risks you're willing to accept.
At FinTech Dynasty, we cut through the noise to give you practical, research-backed guidance on protecting your digital assets. No price predictions. No hype. Just the technical understanding you need to make informed decisions about your own security.
This guide breaks down the core differences between hot and cold storage, explains the security tradeoffs of each approach, and helps you determine which method fits your situation. By the end, you'll have a clear framework for deciding how to store your crypto safely.
What hot and cold wallets really are
A cryptocurrency wallet doesn't actually store your coins. Instead, it holds the private keys that prove ownership of your digital assets on the blockchain. The hot wallet vs cold wallet distinction comes down to one factor: whether those private keys ever touch an internet-connected device during normal use.
Hot wallets: internet-connected storage
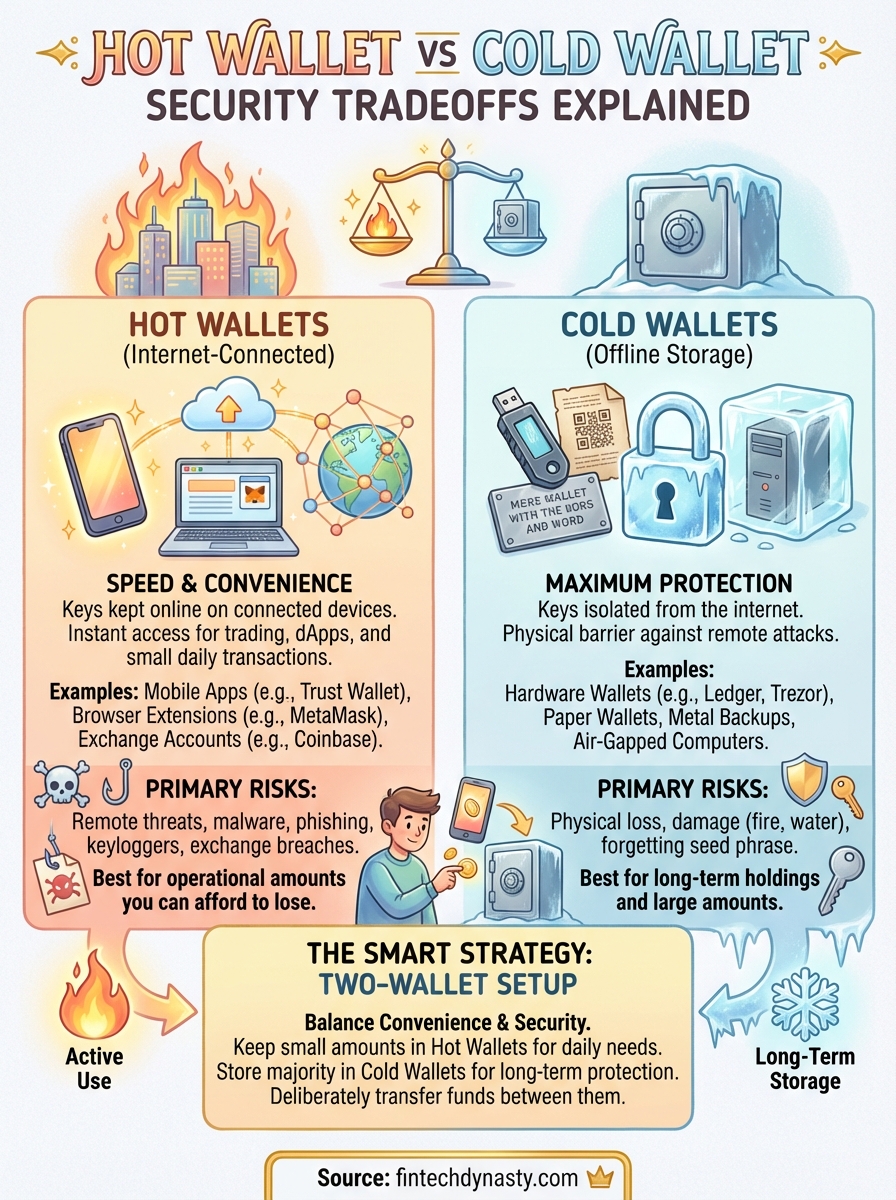
Hot wallets keep your private keys on a device with active internet access. This includes mobile wallet apps, browser extensions, desktop software, and exchange accounts. Your keys remain in digital form on a computer, phone, or server that can connect to the web at any moment.
The connection creates convenience. You can send crypto instantly, interact with decentralized applications, and check balances without additional hardware. Popular hot wallet examples include MetaMask (browser extension), Trust Wallet (mobile app), and Exodus (desktop software).
Hot wallets trade offline protection for instant access, keeping your keys on internet-connected devices where speed matters more than maximum security.
Exchange accounts like Coinbase and Kraken also function as hot wallets when you leave funds there. The exchange controls the private keys on your behalf, storing them on centralized servers that maintain constant connectivity for trading and withdrawals.
Cold wallets: offline key storage
Cold wallets isolate your private keys from any internet-connected environment. The keys never exist on a device that can go online during normal operation. This physical separation blocks remote attacks and malware from ever reaching your actual credentials.
Hardware wallets like Ledger and Trezor represent the most common cold storage method. These dedicated devices generate and store keys internally, keeping them completely offline even when you plug the device into a computer to sign transactions. The signing happens inside the isolated chip, and only the signed transaction (not your keys) passes to the connected device.
Paper wallets take the concept further by printing your private keys on physical paper. You generate the keys on an offline computer, print them, then destroy all digital copies. Steel plates and metal backups offer similar offline storage with greater durability against fire and water damage.
Air-gapped computers provide another cold storage option. You dedicate a device that never connects to any network, generating and storing keys in this permanently offline environment. Each transaction requires manual transfer of data via USB drive or QR code scanning between the offline and online devices.
Why the hot vs cold choice matters
Your storage decision directly determines which attack vectors can reach your crypto. The hot wallet vs cold wallet choice isn't about preference or brand loyalty. It maps to fundamentally different security models that expose you to separate threat categories.
Attack surface differences
Hot wallets face remote threats constantly. Hackers can attempt to breach your device through malware, phishing sites, compromised applications, or network attacks without ever being near you physically. Your keys exist in an internet-connected environment where thousands of automated attacks scan for vulnerabilities every day.
Cold wallets eliminate remote attack vectors entirely. An attacker would need physical access to your hardware device, paper backup, or air-gapped computer to steal your keys. This reduction in attack surface matters significantly. You shift from defending against global threats to managing local security within your control.
The storage method you choose determines whether hackers around the world can attempt to steal your crypto or whether they must physically reach your backup.
Loss and recovery scenarios
Your backup strategy changes based on storage type. Hot wallet compromises often happen instantly and silently. Malware can extract your seed phrase while you type it, sending your keys to an attacker before you realize anything went wrong. You might discover the theft only after seeing an unauthorized transaction on the blockchain.
Cold storage failures typically stem from physical loss or damage. You forget where you stored your seed phrase, your hardware wallet breaks, or a fire destroys your paper backup. These scenarios give you more control. You determine the physical security measures around your backups rather than trusting device software to resist sophisticated remote attacks.
Hot wallets: best uses, risks, and examples
Hot wallets serve situations where speed and accessibility outweigh maximum security. You need instant access to spend crypto, interact with decentralized applications, or manage funds that you actively trade. The hot wallet vs cold wallet decision for daily operations typically favors hot storage when amounts stay small relative to your total holdings.
When hot wallets make sense
Daily transactions require hot wallet convenience. You pay for goods, tip content creators, or move funds between exchanges without waiting for hardware devices or offline signing processes. Active traders keep operating capital in hot wallets to execute trades quickly when market conditions shift.
Decentralized finance protocols demand hot wallet connections. You cannot interact with lending platforms, liquidity pools, or smart contracts using cold storage alone. The blockchain needs your signature in real time, which requires keys on an internet-connected device running the application interface.
Hot wallets excel when you need crypto to work like cash in your pocket, available instantly but held in amounts you can afford to lose.
Security risks you accept
Malware poses the primary threat. Keyloggers capture your password or seed phrase as you type it. Screen recording software steals your recovery words during wallet setup. Clipboard hijackers replace copied addresses with attacker-controlled wallets, redirecting your transactions before you notice.
Phishing attacks target hot wallet users constantly. Fake wallet websites clone legitimate interfaces to capture your credentials. Browser extensions masquerade as popular wallets while harvesting private keys in the background. Your device security determines your wallet security.
Popular hot wallet options
MetaMask dominates browser-based Ethereum storage. Trust Wallet provides mobile access across multiple blockchains. Exodus offers desktop software with built-in exchange features. Each keeps your keys on the connected device, trading security for immediate functionality.
Cold wallets: options, setup, and safe storage
Cold storage removes your private keys from any internet-connected device, creating a physical barrier between your crypto and remote attackers. The hot wallet vs cold wallet security gap widens dramatically here. You accept reduced convenience in exchange for protection that eliminates entire categories of digital theft.
Hardware wallet fundamentals
Dedicated hardware devices generate and store your keys in an isolated environment. Ledger uses a secure element chip that never exposes your private keys, even when you connect the device to a compromised computer. Trezor employs open-source firmware that you can audit yourself, though keys remain vulnerable during firmware updates without additional precautions.

You plug the device into your computer only when signing transactions. The signing process happens inside the hardware, and only the completed signature passes to your computer. Your keys never leave the device, blocking malware from capturing them during normal operation.
Paper and metal backups
Paper wallets provide the simplest cold storage method. You generate a key pair on an offline computer, print the private key and public address, then destroy all digital copies. Your backup exists only on physical paper, immune to remote hacking attempts.
Metal backups solve paper's durability problem. Steel plates withstand fire up to 1,800 degrees and survive water damage that would destroy paper. You stamp or engrave your seed phrase into metal, creating a backup that lasts decades without degradation.
Cold storage shifts your security focus from defending against global hackers to managing physical access and backup redundancy in locations you control.
Setup and initial security
You generate your seed phrase during first-time setup. Write down all 12 or 24 words in order on paper, never taking a photo or storing them digitally. Create multiple physical copies and store them in separate secure locations. Test your backup by recovering the wallet on the same device before sending funds, confirming you recorded the recovery phrase correctly.
How to decide and run a two-wallet setup
Most crypto holders benefit from using both storage types simultaneously. You keep small amounts in hot wallets for daily use while securing the majority of your holdings in cold storage. This split approach balances the hot wallet vs cold wallet tradeoff by matching each storage method to its strengths.
Allocation strategy by risk
Your risk tolerance determines the split percentage. Conservative holders keep 95% or more in cold storage, moving funds to hot wallets only when needed for specific transactions. Active users might maintain 20-30% hot for regular operations while cold-storing their long-term holdings.
Calculate your hot wallet maximum by asking what amount you could lose without financial hardship. Your phone could get stolen, malware could compromise your computer, or a phishing attack could succeed. Never exceed this threshold in any internet-connected wallet, regardless of convenience.
Your hot wallet should hold only what you need for the next week or month of activity, treating it like the cash in your physical wallet while your cold storage acts as your savings account.
Moving between wallets safely
Transfer funds from cold to hot storage deliberately, not reactively. Plan your spending needs in advance and move appropriate amounts during a single session. This minimizes how often you expose your cold wallet to a connected device, reducing attack opportunities.
Verify receiving addresses character by character before confirming transfers. Malware can replace copied addresses with attacker-controlled wallets, redirecting your crypto during the brief moment between cold and hot storage. Double-check the first six and last six characters at minimum, comparing them against your verified hot wallet address stored separately.
Test large transfers with small amounts first. Send $20 worth of crypto, confirm it arrives correctly, then proceed with the full amount you need to move.
Final thoughts
The hot wallet vs cold wallet decision reduces to a single question: how much security do you need for the crypto you're protecting? Hot wallets serve daily operations where speed matters. Cold wallets protect holdings you intend to keep long-term without frequent access.
Most successful crypto holders don't choose one method exclusively. They run both simultaneously, moving funds between storage types based on immediate needs. Your hot wallet handles transactions and interactions. Your cold wallet secures the bulk of your wealth against remote attacks.
Start by moving your long-term holdings to cold storage today. Choose a hardware wallet, set it up correctly, and store multiple backup copies in separate locations. Keep only operational amounts in hot wallets, treating them like physical cash you can afford to lose.
FinTech Dynasty provides detailed hardware wallet comparisons and security guides to help you implement these strategies correctly. Visit our platform for independent reviews and step-by-step tutorials on protecting your digital assets.
